Explore Your Redis Memory Usage with an Interactive Map
—Memetria shows you large keys, memory leaks, old keys, and other potential problems quickly. Try it today without a credit card.
Memetria Monitoring for Redis™* works by connecting to your Redis server from one of several
monitoring servers in Amazon's us-east-1 EC2 Region and recording details
on your server's performance. Basic functionality requires only the
PING, SLOWLOG, and INFO commands,
Memory scanning and other features require broader command access.
Memetria connects from any one of the following IPs:
52.4.225.19852.22.9.21052.22.8.15552.72.75.24952.73.73.70If your network configuration requires CIDR notation,
append a mask of/32 for each IP address, e.g. 52.4.225.198/32:
Find the set of instructions below most appropriate for your setup to allow Memetria to access your Redis server.
Questions? We're happy to help by email or the in-app support system.
You can add the following rules to your Security Group to allow Memetria to connect, using the port of your Redis database:
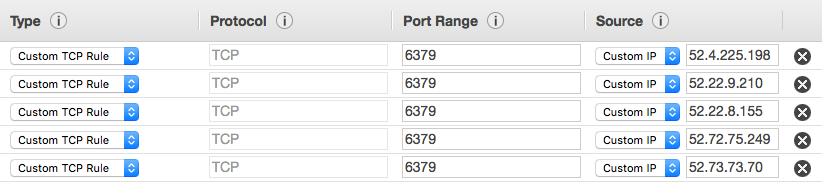
Allow the each of the IPs above to access your Redis database's port in your ACL's
"Inbound Rules" tab, by specifying the CIDR address of each IP (e.g. 52.4.225.198/32).
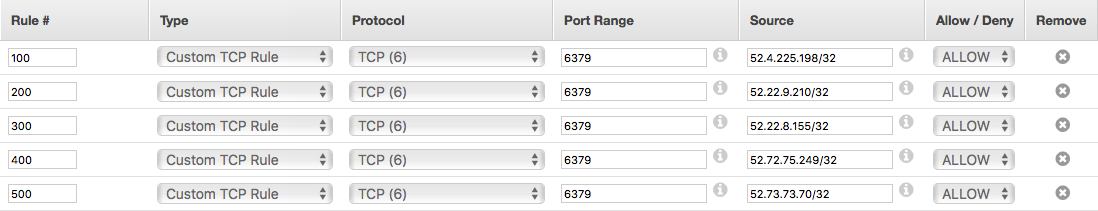
You might need to configure your VPC Security Groups with the instructions above also.
Heroku Private Spaces do not allow external connections for data services by default, but they can be
enabled using Trusted IP ranges for data services.
Once that feature is enabled, you can add each of Memetria Monitor's IPs (listed at the top of this page) with a /32 CIDR suffix, e.g. 52.4.225.198/32.
Due to AWS restrictions, we do not currently support ElastiCache directly.
That said, you can create a NAT instance inside your VPC that can forward Memetria traffic to your ElastiCache servers. See AWS's "Accessing ElastiCache Resources from Outside AWS" page for more information. Once your NAT instance is running, you can use Security Groups, Network ACLs, firewall rules, or iptables rules to restrict access to Memetria.
To allow Memetria access to your server through a firewall, you'll want to allow access to the IP list above through to your Redis database's port (6379 by default). The specific steps will vary depending on your setup, but we've included two of the most common options (ufw and iptables) below:
ufw (Uncomplicated Firewall) is the default firewall tool for Ubuntu. Run the following to allow Memetria to connect to your server, changing "6379" to the correct port for your Redis database:
sudo ufw allow proto tcp from 52.4.225.198 to any port 6379 sudo ufw allow proto tcp from 52.22.9.210 to any port 6379 sudo ufw allow proto tcp from 52.22.8.155 to any port 6379 sudo ufw allow proto tcp from 52.72.75.249 to any port 6379 sudo ufw allow proto tcp from 52.73.73.70 to any port 6379
iptables and its successor nft can be tricky, and we're reluctant to provide instructions
that might be copy-pasted and cause more problems than they solve.
The short answer here is that you need
to Accept Input TCP on the port used by your Redis database (default 6379) from
each of the Sources listed at the top of this document (using CIDR notation, e.g.
52.4.225.198/32).
We like these docs on iptables:
Memetria shows you large keys, memory leaks, old keys, and other potential problems quickly. Try it today without a credit card.